The cannabis industry’s advancement towards legalization continues to dominate national headlines, from the stance of incoming Attorney General Merrick Garland to deprioritize enforcement of low-level cannabis crimes, Senate Majority Leader Chuck Schumer’s continued advocacy, to the recent passing of legislation in New York, New Mexico and Virginia (the first in the South) to authorize adult-use cannabis. While these updates are likely to intrigue customers and investors alike, they are also sure to draw the attention of cyber criminals who could look at the relative youth of the industry, as well as its rapid growth, as a prime target of opportunity for nefarious acts.
In order to understand risk mitigation best practices across a wide spectrum of private sector industries, this article will first identify the current security environment in order to understand the threats, briefly highlight specific case studies and assess the risks and identify methods that individual organizations, as well as the cannabis industry as a whole, can take action to enhance security and preparedness and to develop resiliency against future attacks.
Understanding the Threats
 For an industry that has operated in a largely cash-based system for much of its existence, the idea of security is not foreign. Typically, these concerns focused on physical security implementation. The topic has received plenty of coverage, including a recent article in this journal articulating Important Security Considerations When Designing Cannabis Facilities. While an audit of physical security measures is a valuable part to any all-hazards threat assessment, securing a growing online network – from email to online finances to connected devices within cannabis facilities – can pose more unfamiliar challenges. When consulted for this article, Patten Wood, a former VP of marketing for a prominent west-coast cannabis retail brand noted: “While the topic of cybersecurity is critically important to customers, businesses, and the industry at large, it isn’t top of mind for many of the cannabis companies that I’ve experienced.” Understanding what risks are present is the first step to mitigating them, so we must first discuss several common cyber threats for the cannabis industry.
For an industry that has operated in a largely cash-based system for much of its existence, the idea of security is not foreign. Typically, these concerns focused on physical security implementation. The topic has received plenty of coverage, including a recent article in this journal articulating Important Security Considerations When Designing Cannabis Facilities. While an audit of physical security measures is a valuable part to any all-hazards threat assessment, securing a growing online network – from email to online finances to connected devices within cannabis facilities – can pose more unfamiliar challenges. When consulted for this article, Patten Wood, a former VP of marketing for a prominent west-coast cannabis retail brand noted: “While the topic of cybersecurity is critically important to customers, businesses, and the industry at large, it isn’t top of mind for many of the cannabis companies that I’ve experienced.” Understanding what risks are present is the first step to mitigating them, so we must first discuss several common cyber threats for the cannabis industry.
- Phishing: Phishing happens when cybercriminals impersonate a trusted individual or entity, typically through email. The goal in this instance is to get the target to share confidential information or download software that can allow unauthorized access into an organization’s network. Phishing is one of the most common types of cyberattacks as it is relatively easy to conduct and surprisingly effective.
- Ransomware Attacks: Ransomware attacks are used to gain access to a computer network and then lock and encrypt either the entire system or certain sets of high-value files, which can compromise important business information, and impact client and vendor privacy. A ransom is then demanded for restoring access, but paying the ransom comes with its own risk as it doesn’t guarantee the files will be restored.
- Cyber Extortion: Similar to ransomware attacks in their design, cyber extortion typically deals with a threat of leaking personal information and will generally demand payment in cryptocurrency in order to maintain their anonymity.
-
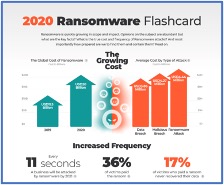
Lumu: 2020 Ransomware Flashcard Remote Access Threats: As 2020 has forced organizations to rethink how they conduct business and shift to more remote operations than they had in the past, it can open up several new threats. According to a survey by IT social network SpiceWorks.com, six out of every ten organizations allow their employees to connect their company-issued devices to public Wi-Fi networks. Utilizing unsecured Wi-Fi networks opens the user up to man-in-the-middle attacks, allowing hackers to intercept company data. Unsecure Wi-Fi also brings the threat of malware distribution. An additional consideration with remote workers is the uptick in cyber attacks against remote access software referred to as remote desktop protocol (RDP) attacks. According to Atlas VPN, RDP attacks skyrocketed 241% in 2020 and we’ve seen numerous RDP attacks against critical infrastructure throughout the pandemic and across all industries.
- Internet of Things (IoT) Leaks: With IoT devices running everything from security systems to automated growing operations, the convenience has been a huge boost for the industry. Unfortunately, many IoT devices don’t have sophisticated built-in security. Another common problem is the tendency of users to keep default passwords upon installation, which can make devices easy for cyber criminals to access. Once they are inside the system, malware can easily be installed, and the actors can move laterally throughout the network.
- Personal and Medical Record Security: Many cyberattacks expose some level of personal data, whether that be customer, employee or vendor information. An extra consideration for retail operations that either treat medical patients, or medical and adult-use customers, is the additional information they must store about their clients. Medical facilities will maintain protected health information (PHI), which are much more valuable on the dark web than personally identifiable information (PII). But even adult use facilities may keep government-issued ID or other additional information above that of a typical retailer, which makes the potential value of their information much more intriguing for a cybercriminal.
Assessing the Risks
Depending on where your organization lies in the seed to sale chain, you will have different levels of risk for various types of attacks. We briefly discussed ransomware attacks earlier. Ransoms can range widely depending on the size of the organization that is attacked, but the ransom alone isn’t the only risk consideration. Businesses must also factor in the cost of downtime (an average of 18 days in 2020) caused by the ransomware when evaluating the impact to business operations, as well as reputation. While small – medium businesses are absolutely at risk, especially given their relative lack of cybersecurity resources and sophistication, a recent trend involves “Big Game Hunting” where cybercriminals are targeting larger organizations with the potential for bigger paydays. Criminals understand that big business can rarely afford major delays, and may be more able and willing to pay, and pay big, for a return to normal operations.
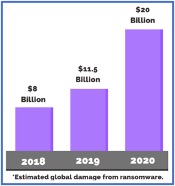
Below are several examples of attacks which have either directly impacted the cannabis industry, or have valuable lessons the industry can learn from.
GrowDiaries: In October 2020 researcher Bob Diachenko discovered that 3.4 million records including passwords, posts, emails and IP addresses were exposed after two open-source application Kibana apps were left exposed online. As a platform for cannabis growers around the world (who are not all growing legally), this type of exposure puts the community at great risk, and can lower user confidence in the product, as well as putting them at personal risk of harm or legal ramifications. The applications being left open is a prime example of either a lack of good cybersecurity policies, or not following through on those policies.
Aurora Cannabis: On December 25th, 2020 Canadian company Aurora Cannabis suffered a data breach when SharePoint and OneDrive were illegally accessed. Included in the data that was compromised was credit card information, government identification, home addresses and banking details. The access point coming through Microsoft cloud software is a prime example of some of the challenges facing businesses who have an increasingly remote workforce yet still need that workforce to access critical (and usually highly sensitive) information.
THSuite: A database owned by seed to sale Point-Of-Sale (POS) software provider THSuite was discovered by researchers in December 2019. The database contained PHI/PII for 30,000 people, with over 85,000 files being exposed. The information that was left accessible included scanned government IDs, personal contact information and medical ID numbers. Clearly this gets into HIPAA territory, which can result in fines of up to $50,000 for every exposed record.
Door Dash: As cannabis delivery apps become more prevalent, it’s good to reference how similar businesses in other industries have been targeted. In May of 2019 nearly 5 million user records were accessed by an unauthorized third party, exposing PII and partial payment card information.
Taking Action
On an organizational level, employee training, password hygiene and malware protection are some of the basic and most important steps that should be taken by all organizations. But, if “knowledge is power,” the best defense for any organization against cyber threats is a well-informed organization- including leadership down to the front-line employees. Excellent tools to assist in this are Information Sharing & Analysis Centers/Organizations (ISACs/ISAOs). ISACs were established under a presidential directive in 1998 to enable critical infrastructure owners and operators to share cyber threat information and best practices. The National Council of ISACs currently has over 20 member ISACs including Real Estate, Water, Automotive and Energy. ISAOs were created by a 2015 executive order to encourage cyber threat information sharing within private industry sectors that fall outside of those listed as “critical infrastructure”. Christy Coffey, vice president of operations at the Maritime and Port Security ISAO (MPS-ISAO) says information sharing enabled by the executive order is critical. “We need to accelerate private sector information sharing, and I believe that the ISAO is the vehicle.”
According to Michael Echols, CEO of the International Association of Certified ISAO’s (IACI) at the Kennedy Space Center, security experts have long understood that threat information sharing can allow for better situational awareness and help organizations better identify common threats and ways to address them. “On the other side, hackers in a very documented way are already teaming up and sharing information on new approaches and opportunities to bring more value (to their efforts).” The ongoing crisis surrounding the Microsoft Exchange Server Vulnerability demonstrates that different cybercriminal groups will work simultaneously to abuse system flaws. As of March 5th it was reported that at least 30,000 organizations in the U.S. – and hundreds of thousands worldwide – have backdoors installed which makes them vulnerable to future attacks, including ransomware.
Below are several links to recent products that have been shared by various ISACs/ISAOs, which are provided as an example of the type of information that is commonly shared via these organizations.
- Joint Cybersecurity Advisory- Compromise of Microsoft Exchange Server
- Health-ISAC’s Hacking Healthcare Weekly Report
- Ford Foundation- Cybersecurity Assessment Tool
If organizations are interested in learning more about enhancing their cybersecurity resiliency through private-sector led information sharing, please reach out to the newly formed Cannabis ISAO at ben@cannabisisao.org








