This is the second part of a series of articles designed to introduce an integrated pest management framework for cannabis cultivation facilities. To see Part One, click here. Part Three comes out next week and covers prioritization and preventative measures. Stay tuned for more!
This is Part 2: Pest Monitoring, Record Keeping, & Communications
Begin your pest identification process with a pest scouting document. You have already mapped out your facility with locations and potential access locations. For each of these pest types and room type assignments (mothers, clone, veg, flower), identify your employee scouts, their scouting methods, scouting frequency and the type of likely pest they are to search for and count.
Insect Types and Tracking Methods
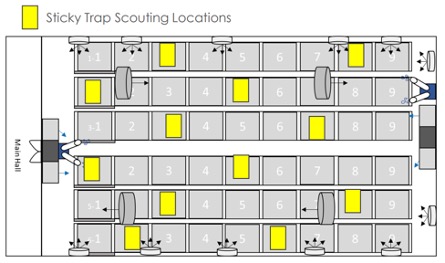
Insect pest types include, but are not limited to, airborne flying or crawling insects, their various egg, lymph, larvae, pupal shells or immature forms. Look for trace remnants, plant damage or feces that let you know they are present in some form. If they are at the mature jumping or flying stage, this can be harder to count, but sticky traps distributed on an even basis around your rooms can make the counting process more consistent from survey to survey.
Note airflows in your rooms and fan locations so migrations can be predicted once an infestation is located.
Insects Can Be Everywhere – Crawlers & Fliers
Insects would like to be everywhere so they come in many types from the obvious flying and crawling types to root-zone microscopic, aquatic, fungal, bacterial or biofilm based. For those of you using soil or media, root-zone insects can be beneficial by digesting and breaking down organic matter into something useful for your plant’s roots (earthworms) or harmful by feeding directly on your plant roots and sucking the life out of your plants from out-of-sight below (nematodes, maggots).
Common pests in a cannabis environment include:
- White flies – Oval shaped eggs on the underside of leaves, nymphs- oval crawlers that suck on the undersides of leaves, larger stage nymphs with pupae shells as they form wings and mature white flies.
- Fungus gnats – Clear eggs deposited in overly wet soil or dead plant matter. Clear or white colored larvae in the soil or media, these worm-like critters go through multiple stages of molting as they grow, eventually pupating into brown cocoons and finally small black or dark flies with clear wings that flutter around your plants and suck on your leaves.
- The dreaded spider mite – Clear, hard to see eggs on the underside of your leaves. These six-legged tiny moving bubbles begin the feeding as larva, add 2 legs in the intermediate and mature nymph stages and finally the oval shaped spider mites that every grower despises, adding their webs around the tops of your plants as their nurseries suck the life out of your flowers.
Insect Transfers of Bacterial Infections

Many crawlers or fliers you may discover in your grow operation do not generate fungus or bacteria on their own. However, they do routinely pick these up along the feeding way and bring them into your shop. Sap-feeding insects like leafhoppers and aphids use their needle mouths to pierce your leaves to suck on the sap that is nourishing your greenery. These insects consume the fluids and transfer bacteria as they feed. Whiteflies fit into this category of leaf sucking bacteria carrying pests. These pests can make your healthy grow rooms look blotchy with color drained out of your canopy.
Obvious symptoms of these flying/hopping pests are sticky leaves, black fungus mold, or yellowing leaves that show up at the bottom of your plants and work their way upward as the infestation progresses. Leaf curling or plant wilting will be visible in the more advanced stages of these pests.
As if crawlers were not bad enough, invisible fungus and bacteria that get into your water supplies can be the worst challenges of any grow.
Water Sourced Bacteria
Baseline testing of your feed water is critical for any facility. This is true whether you are using surface water, well water or municipal water. Please see the water tutorials on the AEssenseGrows website for details on how to test your water sources and what to look for in the mineral content.
Regardless of your water source, bacteria can be present directly in your water supply, or it can be introduced from infected plant materials from one of your suppliers. Pythium, fusarium and the latest plague, hop latent viroid, are some of the most common threats that attack your plants from your water or soil sources. These can come from your wells, feed lines or plant materials.
Reverse osmosis (RO) is a typical method to clear water of most pathogens and bacteria using water that is pressed through filters with very small membrane apertures. These small openings usually stop impurities, salts and microorganisms. Of course, these systems come in many different types and they have to be maintained to keep their performance quality. Don’t take shortcuts on your RO system.
Once your water source is clean, strict hygiene procedures for tools, equipment and plumbing are the best way to minimize these threats to your plants downstream from your water source. These cleaning efforts are not a guarantee. Pests can still get into even the best facilities. Symptoms of these maladies vary, but root rot, stunted growth, wilting, discolored roots or leaves, and in some cases, the quick death of your plants is possible depending on the critter.
Use your scouting regimen and your data mapping to locate infestations before they expand and damage your facility. Isolate outbreaks and take appropriate measures to address the pests. We will give you suggestions on prioritization and preventative measures to take in the next chapter.

Pythium is one of the most commonly harbored soil or water carried pests. When it is present and gets into your plants through cuts, natural openings, root surfaces or leaves on weakened plants, it can be devastating. In hydroponic systems, dirty looking brown roots evolve into full root rot if not addressed. Pythium is often the cause. In soil operations, pythium often shows up as wilting or yellowing patches on leaves.
Your lab testing partners are your friends when it comes to bacterial or fungal infections. Many diseases can resemble one another. It is not hard to misdiagnose environmental stress such as overheating or overwatering for a bacterial problem. Test results are necessary to accurately diagnose a problem.
Truly Airborne Molds & Mildews
Pythium and fusarium are not just present in water. They can also be airborne. Grey mold (botrytis) and powdery mildew are also common airborne pests. Proper humidity, air movement, air filtration and sterilization using HEPA (High-Efficiency Particulate Air) filters, activated carbon filters (also filter smells) and UV light sterilization can minimize these problems in your grow. Powdery mildew is the primary evil spore in this category. Airflow and regular cleaning to discourage fungal growth is the best way to limit these pests.
In conclusion, this week
Now that we have talked about identification (and clearly, this is not an exhaustive list), we will move into how to build in the cultural methods to prevent these problems from taking hold and ruining your business. In later chapters, we will dive into prioritization, treatment and control options for infestations, finally moving into control actions and emergency response.
Your integrated management response is how you pull all of this together and use your IPM procedures to increase your profitability. For the complete white paper on Integrated Pest Management Recommendations, download the document here.
Part three comes out next week and will delve into the world of Preventative Measures. Stay tuned for more!