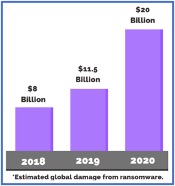
Many experts agree that of all pests threatening the cannabis industry, rodents are the most dangerous. Not only do they chew on cannabis plants and ruin crops at an incredible rate, they also contaminate product with their urine and feces. Rodents post a serious threat to cannabis facilities at every level of the supply chain.
Rodents’ incisor teeth never stop growing; left untouched, a rat’s incisor teeth would grow 4 inches in a year*. For this reason, they must constantly gnaw on things around them to wear them down. Unfortunately for cannabis growers, the woody stalks of cannabis plants present a perfect target. The destructive power of rodents cannot be overstated – creatures that can gnaw through plastic, wood, aluminum, brick, cement and even lead will make very short work of cannabis crops.
The notion that growing cannabis indoors will protect it from rodents is a misconception. Their destructive gnawing power makes rodents highly adept at getting inside buildings. Rodents can enter a building through an opening as small as 1/4 inch, and they will use any means necessary to reach the food and shelter that a heated building provides. In addition to squeezing through minuscule openings, rats and mice can climb wires and rough surfaces, jump considerable distances and tread water for several days.

And once they are inside, it is already too late. Pest control experts worldwide agree that exclusion – the technical term for using physical barriers to prevent rodents from entering a building vs. trying to remove them once inside – is the safest, most effective approach to rodent control. This is because once rodents have gained entry, they will contaminate – and multiply – at an alarming rate.
In one year, two mice could potentially multiply into more than 5,000 mice and two rats could become 1,250. In that same year, a single rat can shed more than half a million body hairs, and a mouse can produce up to 18,000 fecal droppings. Rodents eat or contaminate at least twenty percent of the world’s food supply each year (according to the Indiana Department of Health) and carry diseases including rat bite fever, hantavirus, leptospirosis, salmonellosis, murine typhus, and even the bubonic plague. According to experts from Total Food Service, “Mice are known to frequently carry salmonella bacteria in their digestive tract, so salmonella can be easily spread through contact with rodent waste. This is true with marijuana [sic]edibles just as it is with other food products.”
Keeping rodents out of cannabis facilities is fundamental to protecting crops and products. The most common rodent entryways include exterior doors, open garage and loading dock doors, windows, air vents, fireplaces and at points where electrical, water, gas, sewer and HVAC lines enter the building. Rats and mice can also gain entry through tiny cracks in the foundation, by gnawing through the standard rubber and vinyl seals on most garage and loading dock doors, and beneath roofing tiles.
Consider the following exclusion best practices highlighted in The Mallis Handbook of Pest Control:
- Safeguard your doors. Wooden doors are continuously vulnerable to the gnawing of rats. Sheet iron flashing should be installed surrounding the door, and any clearance below the door must be smaller than 3/8 inch. All doors should remain closed when not in use and be fitted with proven, specialized rodent-proof door sweeps.
- Ventilator grills and windows should be protected with proper and proven exclusion materials, ensuring any voids or cracks are filled.
- Defective drain pipes provide a transportation pipeline for rodents. A perforated metal cover should be cemented over the drain pipe, and any small openings surrounding the drain where it enters the building should be patched or filled with proven exclusion material.
- Large sidewalk cracks should be sealed as these crevices allow rodents to access a building’s foundation, enabling them to more easily search for entry points. Foundation walls can be protected with barriers of metal, concrete, or brick around and below the foundation.
- Circular rat guards should be placed around all vertical wires and pipes.
- Ensure that cracked or broken roofing tiles are identified and replaced in a timely manner, and utilize proven exclusion material to fill any voids.
It’s also critical that only proven, rodent-proof exclusion materials be utilized to seal entry points. Caulk, mortar and spray foam offer almost zero protection against the gnawing power of rodents. Steel wool is often used for filling cracks and crevices, but will eventually rust and break down, rendering it useless against rodents. All exclusion materials should be made of stainless steel or other permanent elements.

Standard rubber door sweeps used for weatherization are not designed to withstand rodent gnawing, making the small gap beneath and around exterior doors a primary rodent entry point. Specialized rodent-proof door sweeps are fundamental to effective rodent exclusion. Xcluder’s Rodent-Proof Door Sweeps feature a core of Xcluder Fill Fabric – a blend of stainless steel and poly-fiber with sharp, coarse fibers that rodents cannot gnaw through – reinforced gaskets for a superior weatherseal and an extended rubber flap to create a flush ground seal against insects and other outdoor contaminants. Installing rodent-proof door sweeps is arguably the single most important step in protecting cannabis facilities from rodent infestation.
Sanitation is also important. Food products of any kind must be stored in sealed containers. Garbage should be collected frequently and stored as far away from the building as possible. Clutter should be avoided in storage areas as crowded shelves and boxes create opportunities for rodent nesting. Roofs and gutters should be free of debris as standing water attracts rodents as well. All trees and landscaping should be trimmed back away from the building to prevent not only rodent burrowing but also access to the roof.
Rodents are not easily deterred, but a well-supported, thorough exclusion plan is the strongest weapon in the fight against rodents. Investing the time and resources to properly safeguard buildings against rodents before a problem is identified is the best way to protect the plants, products and personnel inside cannabis facilities.